Access Management: Difference between revisions
No edit summary |
mNo edit summary |
||
| Line 1: | Line 1: | ||
<seo metakeywords="itil access management, access management itil, itil access management process, access management process" metadescription="Access Management: ITIL process definition - subprocesses - Additional information on ITIL Access Management." /> | |||
<imagemap> | |||
Image:ITIL-Wiki-de-es.jpg|DE - ES - Access Management|100px | |||
rect 0 0 50 30 [https://wiki.de.it-processmaps.com/index.php/Access_Management diese Seite auf Deutsch] | |||
rect 50 0 100 30 [https://wiki.es.it-processmaps.com/index.php/ITIL_Gestion_del_Acceso esta página en español] | |||
desc none | |||
</imagemap> | |||
<br style="clear:both;"/> | |||
== ITIL Access Management: Overview == | |||
'''Process Objective''': To grant authorized users the right to use a service, while preventing access to non-authorized users. The Access Management processes essentially executes policies defined in IT Security Management. Access Management is sometimes also referred to as Rights Management or Identity Management. | '''Process Objective''': To grant authorized users the right to use a service, while preventing access to non-authorized users. The Access Management processes essentially executes policies defined in [[IT Security Management]]. Access Management is sometimes also referred to as ''Rights Management'' or ''Identity Management''. | ||
'''Part of''': [[ITIL V3 Service Operation|Service Operation]] | '''Part of''': [[ITIL V3 Service Operation|Service Operation]] | ||
'''Process Owner''': [[ | '''Process Owner''': [[Access Management#Additional Information on Access Management|Access Manager]] | ||
==ITIL | == ITIL Access Management: Process Definition == | ||
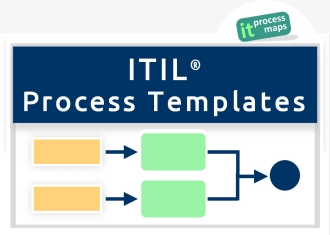
[[Image:Itil-access-management.jpg|thumb=overview_access_management_itilv3_thumb.jpg|left|[https://wiki.en.it-processmaps.com/images/pdf/process_overview_access_management_itilv3.pdf ITIL Access Management]]] | |||
Access Management was added as a new process to ITIL V3. The decision to include this dedicated process was motivated by IT security reasons, as granting access to IT services and applications only to authorized users is of high importance from an IT Security viewpoint. | |||
The following sub-processes are part of [[Access Management|ITIL Access Management]]: | |||
<br style="clear:both;"/> | |||
=== Sub-Processes === | |||
;Maintain Catalogue of User Roles and Access Profiles | ;Maintain Catalogue of User Roles and Access Profiles | ||
:Process Objective: To make sure that the catalogue of User Roles and | :Process Objective: To make sure that the catalogue of [[Access Management#User Role|User Roles]] and [[Access Management#User Role Access Profiles|User Role Access Profiles]] is still appropriate for the services offered to customers, and to prevent unwanted accumulation of [[Access Management#Access Rights|access rights]]. | ||
;Manage User Access Requests | ;Manage User Access Requests | ||
:Process Objective: To process requests to add, change or revoke access rights, and to make sure that only authorized users are granted the right to use a service. | :Process Objective: To process [[Access Management#Request for Access Rights|requests to add, change or revoke access rights]], and to make sure that only authorized users are granted the right to use a service. | ||
===== Downloads ===== | |||
Use the following links to open the process overview of Access Management showing the most important interfaces: | |||
* [[Media:Itil-access-management.jpg|ITIL Access Management (.JPG)]] | |||
* [https://wiki.en.it-processmaps.com/images/pdf/process_overview_access_management_itilv3.pdf ITIL Access Management (.PDF)]'' | |||
=== ITIL Terms: Access Management === | |||
;<span id="Access Rights">Access Rights</span> | |||
:A set of data defining what services a user is allowed to access. This definition is achieved by assigning the user, identified by his User Identity, to one or more User Roles. | |||
;<span id="Request for Access Rights">Request for Access Rights</span> | |||
:A request to grant, change or revoke the right to use a particular service or access certain assets. | |||
;<span id="User Identity Record">User Identity Record</span> | |||
:A set of data with all the details identifying a user or person. It is used to grant rights to that user or person. | |||
;<span id="User Identity Request">User Identity Request</span> | |||
:A request to create, modify or delete a User Identity. | |||
;<span id="User Role">User Role</span> | |||
:A role as part of a catalogue or hierarchy of all the roles (types of users) in the organization. Access rights are based on the roles that individual users have as part of an organization. | |||
;<span id="User Role Access Profile">User Role Access Profile</span> | |||
:A set of data defining the level of access to a service or group of services for a certain type of user ("User Role"). User Role Access Profiles help to protect the confidentiality, integrity and availability of assets by defining what information computer users can utilize, the programs that they can run, and the modifications that they can make. | |||
;<span id="User Role Requirements">User Role Requirements</span> | |||
:Requirements from the business side for the catalogue or hierarchy of user roles (types of users) in the organization. Access rights are based on the roles that individual users have as part of an organization. | |||
== Additional Information on Access Management == | |||
==== ITIL Roles ==== | |||
;Access Manager - Process Owner | |||
:The Access Manager grants authorized users the right to use a service, while preventing access to non-authorized users. | |||
:The Access Manager essentially executes policies defined in IT Security Management. | |||
<i><small>[[Main Page|Home]] > [[ITIL Processes]] > [[ITIL V3 Service Operation|Service Operation]] > [[Access Management|ITIL Access Management]]</small></i> | |||
<!-- This page is assigned to the following categories: --> | |||
[[Category:ITIL V3]][[Category:ITIL process]][[Category:Service Operation|Access Management]][[Category:Access Management|!]] | |||
<!-- --- --> | |||
Revision as of 10:34, 13 July 2011
<seo metakeywords="itil access management, access management itil, itil access management process, access management process" metadescription="Access Management: ITIL process definition - subprocesses - Additional information on ITIL Access Management." />

ITIL Access Management: Overview
Process Objective: To grant authorized users the right to use a service, while preventing access to non-authorized users. The Access Management processes essentially executes policies defined in IT Security Management. Access Management is sometimes also referred to as Rights Management or Identity Management.
Part of: Service Operation
Process Owner: Access Manager
ITIL Access Management: Process Definition
Access Management was added as a new process to ITIL V3. The decision to include this dedicated process was motivated by IT security reasons, as granting access to IT services and applications only to authorized users is of high importance from an IT Security viewpoint.
The following sub-processes are part of ITIL Access Management:
Sub-Processes
- Maintain Catalogue of User Roles and Access Profiles
- Process Objective: To make sure that the catalogue of User Roles and User Role Access Profiles is still appropriate for the services offered to customers, and to prevent unwanted accumulation of access rights.
- Manage User Access Requests
- Process Objective: To process requests to add, change or revoke access rights, and to make sure that only authorized users are granted the right to use a service.
Downloads
Use the following links to open the process overview of Access Management showing the most important interfaces:
ITIL Terms: Access Management
- Access Rights
- A set of data defining what services a user is allowed to access. This definition is achieved by assigning the user, identified by his User Identity, to one or more User Roles.
- Request for Access Rights
- A request to grant, change or revoke the right to use a particular service or access certain assets.
- User Identity Record
- A set of data with all the details identifying a user or person. It is used to grant rights to that user or person.
- User Identity Request
- A request to create, modify or delete a User Identity.
- User Role
- A role as part of a catalogue or hierarchy of all the roles (types of users) in the organization. Access rights are based on the roles that individual users have as part of an organization.
- User Role Access Profile
- A set of data defining the level of access to a service or group of services for a certain type of user ("User Role"). User Role Access Profiles help to protect the confidentiality, integrity and availability of assets by defining what information computer users can utilize, the programs that they can run, and the modifications that they can make.
- User Role Requirements
- Requirements from the business side for the catalogue or hierarchy of user roles (types of users) in the organization. Access rights are based on the roles that individual users have as part of an organization.
Additional Information on Access Management
ITIL Roles
- Access Manager - Process Owner
- The Access Manager grants authorized users the right to use a service, while preventing access to non-authorized users.
- The Access Manager essentially executes policies defined in IT Security Management.
Home > ITIL Processes > Service Operation > ITIL Access Management