Access Management: Difference between revisions
No edit summary |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
<itpmch><title>Access Management | IT Process Wiki</title> | <itpmch><title>Access Management | IT Process Wiki</title> | ||
<meta name="keywords" content="itil access management, access management itil, itil access management process, access management process" /> | <meta name="keywords" content="itil access management, access management itil, itil access management process, access management process" /> | ||
<meta name="description" content="Access Management: ITIL process | <meta name="description" content="Access Management aims to grant authorized users the right to use a service, while preventing access to non-authorized users. This ITIL process essentially executes policies defined in Information Security Management. Access Management is sometimes also referred to as 'Rights Management' or 'Identity Management'." /> | ||
<meta property="og:url" content="https://wiki.en.it-processmaps.com/index.php/Access_Management" /> | |||
<meta property="og:title" content="Access Management | IT Process Wiki" /> | |||
<meta property="og:description" content="Access Management aims to grant authorized users the right to use a service, while preventing access to non-authorized users. This ITIL process essentially executes policies defined in Information Security Management. Access Management is sometimes also referred to as 'Rights Management' or 'Identity Management'." /> | |||
<meta property="og:site_name" content="IT Process Wiki - the ITIL® Wiki"> | |||
<meta property="og:type" content="article" /> | |||
<meta property="article:publisher" content="https://www.facebook.com/itprocessmaps" /> | |||
<meta property="fb:admins" content="100002035253209" /> | |||
<meta property="fb:admins" content="100002592864414" /> | |||
<meta property="og:image" content="https://wiki.en.it-processmaps.com/images/1/1f/Access-management-itil.jpg" /> | |||
<meta property="og:image:width" content="1200" /> | |||
<meta property="og:image:height" content="900" /> | |||
<link href="https://plus.google.com/108613479011811316823/posts" rel="publisher" /> | |||
</itpmch> | </itpmch> | ||
<imagemap> | <imagemap> | ||
Image:ITIL-Wiki-de-es.jpg|DE - ES - Access Management| | Image:ITIL-Wiki-de-es.jpg|right|DE - ES - Access Management|163px | ||
rect 0 | rect 81 0 114 36 [https://wiki.de.it-processmaps.com/index.php/Access_Management diese Seite auf Deutsch] | ||
rect | rect 115 0 163 36 [https://wiki.es.it-processmaps.com/index.php/ITIL_Gestion_del_Acceso esta página en español] | ||
desc none | desc none | ||
</imagemap> | </imagemap> | ||
<br style="clear:both;"/> | <br style="clear:both;"/> | ||
'''<span id="Overview">Objective:</span>''' <html><span id="md-webpage-description" itemprop="description"><i>Access Management</i> aims to grant authorized users the right to use a service, while preventing access to non-authorized users. This ITIL process essentially executes policies defined in <a href="https://wiki.en.it-processmaps.com/index.php/IT_Security_Management" title="IT Security Management">Information Security Management</a>. Access Management is sometimes also referred to as 'Rights Management' or 'Identity Management'.</span></p> | |||
<p><b>Part of</b>: <a href="https://wiki.en.it-processmaps.com/index.php/ITIL_Service_Operation" title="ITIL Service Operation">Service Operation</a></html> | |||
'''<span id="Overview">Objective:</span>''' <html><span | |||
<p><b>Part of</b>: <a | |||
'''Process Owner''': [[Access Management#Access Manager|Access Manager]] | '''Process Owner''': [[Access Management#Access Manager|Access Manager]] | ||
| Line 23: | Line 32: | ||
==Process Description== | ==Process Description== | ||
Access Management | [[Image:Access-management-itil.jpg|right|thumb|500px|alt=Access Management ITIL|link=https://wiki.en.it-processmaps.com/index.php/File:Access-management-itil.jpg|[https://wiki.en.it-processmaps.com/images/pdf/process_overview_access_management_itilv3.pdf ITIL Access Management (.pdf)]]] | ||
Access Management has been added as a new process to ITIL V3. The decision to include this dedicated process was motivated by Information security reasons, as granting access to IT services and applications only to authorized users is of high importance from an [[IT Security Management|Information Security]] viewpoint. | |||
In ITIL 2011 an interface between Access Management and Event Management has been added, to emphasize that (some) Event filtering and correlation rules should be designed by Access Management to support the detection of unauthorized access to services. The process overview of [[Media:Access-management-itil.jpg|ITIL Access Management]] shows the key information flows (see fig. 1). | |||
In | |||
A | A specific activity has been added to revoke [[Access Management#Access Rights|access rights]] if required. And it has been made clearer in the Request Fulfilment and Incident Management processes that the requester's authorization must be checked. | ||
[[ITIL 4]] refers to 'Access Management' as a [[ITIL_4#General_management_practices|general management practice]] - as part of "Information security management". | |||
<p style="clear:both;"> </p> | |||
<p> </p> | |||
==Sub-Processes== | ==Sub-Processes== | ||
| Line 40: | Line 48: | ||
<p><span itemprop="name" content="Access Management sub-processes:">These are the <strong class="selflink">ITIL Access Management</strong> sub-processes and their process objectives:</span> | <p><span itemprop="name" content="Access Management sub-processes:">These are the <strong class="selflink">ITIL Access Management</strong> sub-processes and their process objectives:</span> | ||
</p> | </p> | ||
<p><b><span id="ITIL_Access_Management_Catalogue" itemprop="itemListElement">Maintenance of Catalogue of User Roles and Access Profiles</span></b> | <p><b><span id="ITIL_Access_Management_Catalogue" itemprop="itemListElement">Maintenance of Catalogue of User Roles and Access Profiles</span></b> | ||
</p> | </p> | ||
<ul><li itemprop="description">Process Objective: To make sure that the catalogue of <a href="/index.php/Access_Management#User_Role" title="Access Management">User Roles</a> and <a href="/index.php/Access_Management#User_Role_Access_Profile" title="Access Management">Access Profiles</a> is still appropriate for the | <ul><li itemprop="description">Process Objective: To make sure that the catalogue of <a href="/index.php/Access_Management#User_Role" title="Access Management">User Roles</a> and <a href="/index.php/Access_Management#User_Role_Access_Profile" title="Access Management">Access Profiles</a> is still appropriate for the services offered to customers, and to prevent unwanted accumulation of <a href="/index.php/Access_Management#Access_Rights" title="Access Management">access rights</a>. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="ITIL_Access_Management_Requests" itemprop="itemListElement">Processing of User Access Requests</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">Process Objective: To process <a href="/index.php/Access_Management#Request_for_Access_Rights" title="Access Management">requests to add, change or revoke access rights</a>, and to make sure that only authorized users are granted the right to use a service. | <ul><li itemprop="description">Process Objective: To process <a href="/index.php/Access_Management#Request_for_Access_Rights" title="Access Management">requests to add, change or revoke access rights</a>, and to make sure that only authorized users are granted the right to use a service. | ||
</li></ul> | </li></ul> | ||
</div><!-- end of schema.org/ItemList --><p></html> | </div><!-- end of schema.org/ItemList --><p></html> | ||
== Definitions == | == Definitions == | ||
| Line 57: | Line 62: | ||
<html><div itemscope="itemscope" itemtype="https://schema.org/ItemList"><!-- define schema.org/ItemList --> | <html><div itemscope="itemscope" itemtype="https://schema.org/ItemList"><!-- define schema.org/ItemList --> | ||
<meta itemprop="itemListOrder" content="Ascending" /> | <meta itemprop="itemListOrder" content="Ascending" /> | ||
<p><span itemprop="name">The following <a href="/index.php/ | <p><span itemprop="name">The following <a href="/index.php/ITIL_Glossary#ITIL_Glossary_A-Z" title="ITIL Glossary">ITIL terms and acronyms</a> (<i>information objects</i>) are used in the Access Management process to represent process outputs and inputs:</span> | ||
</p> | </p> | ||
<p><b><span id="Access_Rights" itemprop="itemListElement">Access Rights</span></b> | <p><b><span id="Access_Rights" itemprop="itemListElement">Access Rights</span></b> | ||
</p> | </p> | ||
<ul><li itemprop="description">A set of data defining what services a user is allowed to access. This definition is achieved by assigning the user, identified by his User Identity, to one or more <a href="/index.php/Access_Management#User_Role" title="Access Management">User Roles</a>. | <ul><li itemprop="description">A set of data defining what services a user is allowed to access. This definition is achieved by assigning the user, identified by his User Identity, to one or more <a href="/index.php/Access_Management#User_Role" title="Access Management">User Roles</a>. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="Request_for_Access_Rights" itemprop="itemListElement">Request for Access Rights</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">A request to grant, change or revoke the right to use a particular service or access certain assets. | <ul><li itemprop="description">A request to grant, change or revoke the right to use a particular service or access certain assets. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="User_Identity_Record" itemprop="itemListElement">User Identity Record</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">A set of data with all the details identifying a user or person. It is used to grant rights to that user or person. | <ul><li itemprop="description">A set of data with all the details identifying a user or person. It is used to grant rights to that user or person. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="User_Identity_Request" itemprop="itemListElement">User Identity Request</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">A request to create, modify or delete a User Identity. | <ul><li itemprop="description">A request to create, modify or delete a User Identity. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="User_Role" itemprop="itemListElement">User Role</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">A role as part of a catalogue or hierarchy of all the roles (types of users) in the organization. <a href="/index.php/Access_Management#Access_Rights" title="Access Management">Access rights</a> are based on the roles that individual users have as part of an organization. | <ul><li itemprop="description">A role as part of a catalogue or hierarchy of all the roles (types of users) in the organization. <a href="/index.php/Access_Management#Access_Rights" title="Access Management">Access rights</a> are based on the roles that individual users have as part of an organization. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="User_Role_Access_Profile" itemprop="itemListElement">User Role Access Profile</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">A set of data defining the level of access to a service or group of services for a certain type of user (<a href="/index.php/Access_Management#User_Role" title="Access Management">User Role</a>). User Role Access Profiles help to protect the confidentiality, integrity and availability of assets by defining what information computer users can utilize, the programs that they can run, and the modifications that they can make. | <ul><li itemprop="description">A set of data defining the level of access to a service or group of services for a certain type of user (<a href="/index.php/Access_Management#User_Role" title="Access Management">User Role</a>). User Role Access Profiles help to protect the confidentiality, integrity and availability of assets by defining what information computer users can utilize, the programs that they can run, and the modifications that they can make. | ||
</li></ul> | </li></ul> | ||
<p><b><span id="User_Role_Requirements" itemprop="itemListElement">User Role Requirements</span></b> | |||
</p> | </p> | ||
<ul><li itemprop="description">Requirements from the business side for the catalogue or hierarchy of user roles (types of users) in the organization. <a href="/index.php/Access_Management#Access_Rights" title="Access Management">Access rights</a> are based on the roles that individual users have as part of an organization. | <ul><li itemprop="description">Requirements from the business side for the catalogue or hierarchy of user roles (types of users) in the organization. <a href="/index.php/Access_Management#Access_Rights" title="Access Management">Access rights</a> are based on the roles that individual users have as part of an organization. | ||
</li></ul> | </li></ul> | ||
</div><!-- end of schema.org/ItemList --><p></html> | </div><!-- end of schema.org/ItemList --><p></html> | ||
==Roles | Responsibilities== | ==Roles | Responsibilities== | ||
| Line 101: | Line 98: | ||
'''<span id="Access Manager">Access Manager - Process Owner</span>''' | '''<span id="Access Manager">Access Manager - Process Owner</span>''' | ||
*The Access Manager grants authorized users the right to use a service, while preventing access to non-authorized users. | *The Access Manager grants authorized users the right to use a service, while preventing access to non-authorized users. | ||
*The Access Manager essentially executes policies defined in Information Security Management. | *The Access Manager essentially executes policies defined in [[IT Security Management|Information Security Management]]. | ||
'''<span id="1st Level Support">1st Level Support</span>''' | |||
* The responsibility of 1st Level Support is to register and classify received Incidents and to undertake an immediate effort in order to restore a failed IT service as quickly as possible. If no ad-hoc solution can be achieved, 1st Level Support will transfer the Incident to expert technical support groups ([[ITIL_Roles#2nd Level Support|2nd Level Support]]). 1st Level Support also processes [[Request_Fulfilment#Service_Request|Service Requests]] and keeps users informed about their Incidents' status at agreed intervals. | |||
<p> </p> | <p> </p> | ||
{| | {| class="wikitable" style="background: white;" | ||
|- | |- | ||
|style=" | |+ style="background:#013b5e; color:#ffffff; font-size: 120%" colspan="3"| '''Responsibility Matrix: ITIL Access Management''' | ||
|- | |- | ||
! style="background:#ffffee; width: | ! style="background:#ffffee; width: 60%; text-align:center" | ITIL Role / Sub-Process | ||
! style="background:# | ! style="background:#eeeeee" | [[Access Management#Access Manager|Access Manager]] | ||
! style="background:#eeeeee" | [[Access Management#1st Level Support|1st Level Support]] | |||
|- | |- | ||
|style="text-align:left;" |[[#ITIL Access Management Catalogue|Maintenance of Catalogue of User Roles and Access Profile]] | |style="text-align:left;" |[[#ITIL Access Management Catalogue|Maintenance of Catalogue of User Roles and Access Profile]] | ||
| A[[Access Management#Accountable|<small>[1]</small>]]R[[Access Management#Responsible|<small>[2]</small>]] | | A[[Access Management#Accountable|<small>[1]</small>]]R[[Access Management#Responsible|<small>[2]</small>]] | ||
| | |||
|- | |- | ||
|style="text-align:left;" |[[#ITIL Access Management Requests|Processing of User Access Requests]] | |style="text-align:left;" |[[#ITIL Access Management Requests|Processing of User Access Requests]] | ||
| | | A | ||
| R[[Access Management#Responsible-delegated|<small>[3]</small>]] | |||
|- | |- | ||
|} | |} | ||
'''Remarks''' | '''Remarks''' | ||
| Line 128: | Line 129: | ||
<span id="Responsible">[2] ''R: Responsible'' according to the RACI Model: Those who do the work to achieve a task within Access Management.</span> | <span id="Responsible">[2] ''R: Responsible'' according to the RACI Model: Those who do the work to achieve a task within Access Management.</span> | ||
< | <span id="Responsible-delegated">[3] According to ITIL, it is quite common for the service desk / 1st level support ''to be delegated responsibility'' for providing access to simple services.</span> | ||
== Process Implementation: Notes == | == Process Implementation: Notes == | ||
| Line 136: | Line 137: | ||
Well-defined interfaces between the business and Access Management are vital to achieve high security standards. Typically, responsibilities of both sides are defined in a dedicated Information Security Policy. This policy would, for example, stipulate that HR is to inform Access Management without delay about employees entering or leaving the company. | Well-defined interfaces between the business and Access Management are vital to achieve high security standards. Typically, responsibilities of both sides are defined in a dedicated Information Security Policy. This policy would, for example, stipulate that HR is to inform Access Management without delay about employees entering or leaving the company. | ||
==Notes== | |||
== | <html>By:  Stefan Kempter <a rel="author" href="https://www.linkedin.com/in/stefankempter"><img style="margin:0px 0px 0px 0px;" src="/images/bookmarking/linkedin.png" width="16" height="16" title="By: Stefan Kempter | Profile on LinkedIn" alt="Author: Stefan Kempter, IT Process Maps GbR" /></a>, IT Process Maps.</p> | ||
< | <p> </p> | ||
</ | |||
<p><small> | <p><small> | ||
<span itemscope="itemscope | <span itemprop="breadcrumb" itemscope itemtype="http://schema.org/BreadcrumbList"> | ||
<a href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Process_Description | <span itemprop="itemListElement" itemscope itemtype="http://schema.org/ListItem"> | ||
</span> | <a itemprop="item" href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Process_Description"> | ||
<span | <span itemprop="name">Process Description</span></a> | ||
<a href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Sub-Processes | <meta itemprop="position" content="1"></span> › | ||
</span> | <span itemprop="itemListElement" itemscope itemtype="http://schema.org/ListItem"> | ||
<span | <a itemprop="item" href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Sub-Processes"> | ||
<a href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Definitions | <span itemprop="name">Sub-Processes</span></a> | ||
</span> | <meta itemprop="position" content="2"></span> › | ||
<span | <span itemprop="itemListElement" itemscope itemtype="http://schema.org/ListItem"> | ||
<a href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Roles_.7C_Responsibilities | <a itemprop="item" href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Definitions"> | ||
<span itemprop="name">Definitions</span></a> | |||
<meta itemprop="position" content="3"></span> › | |||
<span itemprop="itemListElement" itemscope itemtype="http://schema.org/ListItem"> | |||
<a itemprop="item" href="https://wiki.en.it-processmaps.com/index.php/Access_Management#Roles_.7C_Responsibilities"> | |||
<span itemprop="name">Roles</span></a> | |||
<meta itemprop="position" content="4"></span> | |||
</span> | </span> | ||
</small></p> | </small></p> | ||
</ | |||
<!-- define schema.org/WebPage --> <span itemscope itemtype="https://schema.org/WebPage" itemref="md-webpage-description"> | |||
<meta itemprop="alternativeHeadline" content="ITIL Access Management" /> | |||
<meta itemprop="name" content="Access Management" /> | |||
<link itemprop="url" href="https://wiki.en.it-processmaps.com/index.php/Access_Management" /> | |||
<meta itemprop="inLanguage" content="en" /> | |||
<link itemprop="citation" href="https://wiki.de.it-processmaps.com/index.php/Access_Management" /> | |||
<link itemprop="citation" href="https://wiki.es.it-processmaps.com/index.php/ITIL_Gestion_del_Acceso" /> | |||
<meta itemprop="Headline" content="Access Management" /> | |||
<link itemprop="isPartOf" href="https://wiki.en.it-processmaps.com/index.php/ITIL_Service_Operation" /> | |||
<link itemprop="primaryImageOfPage" href="https://wiki.en.it-processmaps.com/images/1/1f/Access-management-itil.jpg" /> | |||
<span id="https://wiki.en.it-processmaps.com/images/1/1f/Access-management-itil.jpg" itemprop="image" itemscope itemtype="https://schema.org/ImageObject"> | |||
<meta itemprop="caption" content="ITIL Access Management"> | |||
<meta itemprop="contentUrl" content="https://wiki.en.it-processmaps.com/images/1/1f/Access-management-itil.jpg" /> | |||
<meta itemprop="width" content="1200" /> | |||
<meta itemprop="height" content="900" /> | |||
<meta itemprop="representativeOfPage" content="true"/> | |||
<meta itemprop="dateCreated" content="2011-10-02" /> | |||
<meta itemprop="dateModified" content="2020-06-20" /> | |||
<span itemprop="thumbnail" itemscope itemtype="https://schema.org/ImageObject"> | |||
<meta itemprop="url" content="https://wiki.en.it-processmaps.com/images/thumb/1/1f/Access-management-itil.jpg/800px-Access-management-itil.jpg" /> | |||
<meta itemprop="width" content="800" /> | |||
<meta itemprop="height" content="600" /> | |||
</span> | |||
<meta itemprop="keywords" content="Access Management" /> | |||
<meta itemprop="keywords" content="ITIL Access Management" /> | |||
</span> | |||
<link itemprop="author" href="https://www.linkedin.com/in/stefankempter" /> | |||
<meta itemprop="author" content="Stefan Kempter" /> | |||
<meta itemprop="creator copyrightHolder publisher" content="IT Process Maps" /> | |||
</span><p></html> | |||
<!-- This page is assigned to the following categories: --> | <!-- This page is assigned to the following categories: --> | ||
[[Category:ITIL V3]][[Category:ITIL | [[Category:ITIL 4]][[Category:ITIL 2011]][[Category:ITIL V3]][[Category:ITIL practice]][[Category:ITIL process]][[Category:Service Operation|Access Management]][[Category:Access Management|!]] | ||
<!-- --- --> | <!-- --- --> | ||
Latest revision as of 12:56, 31 December 2023

Objective: Access Management aims to grant authorized users the right to use a service, while preventing access to non-authorized users. This ITIL process essentially executes policies defined in Information Security Management. Access Management is sometimes also referred to as 'Rights Management' or 'Identity Management'.
Part of: Service Operation
Process Owner: Access Manager
Process Description
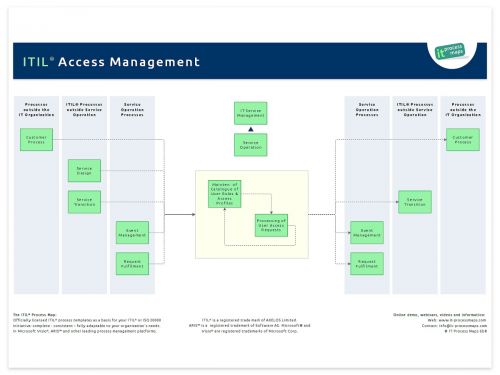
Access Management has been added as a new process to ITIL V3. The decision to include this dedicated process was motivated by Information security reasons, as granting access to IT services and applications only to authorized users is of high importance from an Information Security viewpoint.
In ITIL 2011 an interface between Access Management and Event Management has been added, to emphasize that (some) Event filtering and correlation rules should be designed by Access Management to support the detection of unauthorized access to services. The process overview of ITIL Access Management shows the key information flows (see fig. 1).
A specific activity has been added to revoke access rights if required. And it has been made clearer in the Request Fulfilment and Incident Management processes that the requester's authorization must be checked.
ITIL 4 refers to 'Access Management' as a general management practice - as part of "Information security management".
Sub-Processes
These are the ITIL Access Management sub-processes and their process objectives:
Maintenance of Catalogue of User Roles and Access Profiles
- Process Objective: To make sure that the catalogue of User Roles and Access Profiles is still appropriate for the services offered to customers, and to prevent unwanted accumulation of access rights.
Processing of User Access Requests
- Process Objective: To process requests to add, change or revoke access rights, and to make sure that only authorized users are granted the right to use a service.
Definitions
The following ITIL terms and acronyms (information objects) are used in the Access Management process to represent process outputs and inputs:
Access Rights
- A set of data defining what services a user is allowed to access. This definition is achieved by assigning the user, identified by his User Identity, to one or more User Roles.
Request for Access Rights
- A request to grant, change or revoke the right to use a particular service or access certain assets.
User Identity Record
- A set of data with all the details identifying a user or person. It is used to grant rights to that user or person.
User Identity Request
- A request to create, modify or delete a User Identity.
User Role
- A role as part of a catalogue or hierarchy of all the roles (types of users) in the organization. Access rights are based on the roles that individual users have as part of an organization.
User Role Access Profile
- A set of data defining the level of access to a service or group of services for a certain type of user (User Role). User Role Access Profiles help to protect the confidentiality, integrity and availability of assets by defining what information computer users can utilize, the programs that they can run, and the modifications that they can make.
User Role Requirements
- Requirements from the business side for the catalogue or hierarchy of user roles (types of users) in the organization. Access rights are based on the roles that individual users have as part of an organization.
Roles | Responsibilities
Access Manager - Process Owner
- The Access Manager grants authorized users the right to use a service, while preventing access to non-authorized users.
- The Access Manager essentially executes policies defined in Information Security Management.
1st Level Support
- The responsibility of 1st Level Support is to register and classify received Incidents and to undertake an immediate effort in order to restore a failed IT service as quickly as possible. If no ad-hoc solution can be achieved, 1st Level Support will transfer the Incident to expert technical support groups (2nd Level Support). 1st Level Support also processes Service Requests and keeps users informed about their Incidents' status at agreed intervals.
| ITIL Role / Sub-Process | Access Manager | 1st Level Support |
|---|---|---|
| Maintenance of Catalogue of User Roles and Access Profile | A[1]R[2] | |
| Processing of User Access Requests | A | R[3] |
Remarks
[1] A: Accountable according to the RACI Model: Those who are ultimately accountable for the correct and thorough completion of the Access Management process.
[2] R: Responsible according to the RACI Model: Those who do the work to achieve a task within Access Management.
[3] According to ITIL, it is quite common for the service desk / 1st level support to be delegated responsibility for providing access to simple services.
Process Implementation: Notes
There are a number of different approaches to implementing Access Management. Depending on the size of an organization the methods applied can be rather complex. In this context, ITIL does not provide a detailed explanation of all aspects of Access Management.
Well-defined interfaces between the business and Access Management are vital to achieve high security standards. Typically, responsibilities of both sides are defined in a dedicated Information Security Policy. This policy would, for example, stipulate that HR is to inform Access Management without delay about employees entering or leaving the company.
Notes
By: Stefan Kempter ![]() , IT Process Maps.
, IT Process Maps.
Process Description › Sub-Processes › Definitions › Roles