IT Security Management: Difference between revisions
| Line 8: | Line 8: | ||
<br style="clear:both;"/> | <br style="clear:both;"/> | ||
== Information Security Management == | <p> </p> | ||
==<span id="Information Security Management">Overview</span>== | |||
''Information Security Management'' aims to ensure the confidentiality, integrity and availability of an organization's information, data and IT services. | '''Objective''': ''Information Security Management'' aims to ensure the confidentiality, integrity and availability of an organization's information, data and IT services. ITIL Security Management usually forms part of an organizational approach to security management which has a wider scope than the IT Service Provider. | ||
'''Part of''': [[ITIL V3 Service Design|Service Design]] | '''Part of''': [[ITIL V3 Service Design|Service Design]] | ||
'''Process Owner''': [[IT Security Management# | '''Process Owner''': [[IT Security Management#Information Security Manager|Information Security Manager]] | ||
<p> </p> | <p> </p> | ||
== Process | == Process Description == | ||
ITIL V3 treats Information Security Management as part of the Service Design core volume, resulting in a better integration of this process into the Service Lifecycle (the previous ITIL version provided guidance on Security Management in a separate book). The process was updated to account for new information security concerns. | |||
[[Image:Itil-security-management.jpg| | [[Image:Itil-security-management.jpg|right|thumb|375px|alt=Information Security Management ITIL|[https://wiki.en.it-processmaps.com/images/pdf/process_overview_it_security_management_itilv3.pdf ITIL Security Management]]] | ||
ITIL does not provide a detailed explanation of all aspects of Information Security Management, as there are dedicated and more detailed standards available (see, for example, ISO 27001). Rather, ITIL highlights the most important activities and assists in identifying interfaces with other Service Management processes. | |||
Following the introduction of Design Coordination in '''''ITIL 2011''''' the information flows have been adapted. The process overview of [[Media:Itil-security-management.jpg|ITIL Security Management (.JPG)]] is showing the most important interfaces (see Figure 1). | |||
<p> </p> | |||
< | |||
== Sub-Processes == | == Sub-Processes == | ||
;Design of Security Controls | These are the Information Management sub-processes and their process objectives: | ||
<p> </p> | |||
;<span id="ITIL Security Management Controls">Design of Security Controls</span> | |||
:Process Objective: To design appropriate technical and organizational measures in order to ensure the confidentiality, integrity, security and availability of an organization's assets, information, data and services. | :Process Objective: To design appropriate technical and organizational measures in order to ensure the confidentiality, integrity, security and availability of an organization's assets, information, data and services. | ||
;Security Testing | ;<span="ITIL Security Management Testing">Security Testing</span> | ||
:Process Objective: To make sure that all security mechanisms are subject to regular testing. | :Process Objective: To make sure that all security mechanisms are subject to regular [[IT Security Management#Test Report|testing]]. | ||
;Management of Security Incidents | ;<span id="ITIL Security Management Incidents">Management of Security Incidents</span> | ||
:Process Objective: To detect and fight attacks and intrusions, and to minimize the damage incurred by security breaches. | :Process Objective: To detect and fight attacks and intrusions, and to minimize the damage incurred by security breaches. | ||
;Security Review | ;<span id="ITIL Security Management Review">Security Review</span> | ||
:Process Objective: To review if security measures and procedures are still in line with risk perceptions from the business side, and to verify if those measures and procedures are regularly maintained and tested. | :Process Objective: To review if security measures and procedures are still in line with risk perceptions from the business side, and to verify if those measures and procedures are regularly maintained and tested. | ||
<p> </p> | <p> </p> | ||
== | == Definitions == | ||
The following ITIL terms and acronyms (''information objects'') are used in ITIL Security Management to represent process outputs and inputs: | |||
<p> </p> | |||
;<span id="Availability-ITSCM-Security-Testing-Schedule">Availability/ ITSCM/ Security Testing Schedule</span> | ;<span id="Availability-ITSCM-Security-Testing-Schedule">Availability/ ITSCM/ Security Testing Schedule</span> | ||
:A schedule for the regular testing of all availability, continuity and security mechanisms, jointly maintained by [[Availability Management|Availability]], [[IT Service Continuity Management|IT Service Continuity]] and [[IT Security Management|Information Security Management]]. | :A schedule for the [[IT Security Management#ITIL Security Management Testing|regular testing]] of all availability, continuity and security mechanisms, jointly maintained by [[Availability Management|Availability]], [[IT Service Continuity Management|IT Service Continuity]] and [[IT Security Management|Information Security Management]]. | ||
;<span id="Security | ;<span id="ITIL Security Management Rules">Event Filtering and Correlation Rules</span> | ||
: | :Rules and criteria used to determine if an Event is significant and to decide upon an appropriate response. Event Filtering and Correlation Rules are typically used by Event Monitoring systems. Some of those rules are defined during the Service Design stage, for example to ensure that Events are triggered when the required service availability is endangered. | ||
;<span id="Security-Report">Information Security Report</span> | ;<span id="ITIL Security Policy">Information Security Policy</span> | ||
:The main Information Security Policy contains an outline of the approach to ensure the security of IT services and systems. It is typically complemented by a set of more [[IT Security Management#Underpinning-Information-Security-Policy|specific underpinning policies]], e.g. policies on e-mail usage or remote system access. The Information Security Policy includes a list of security-related risks and existing or planned Security Controls to address those risks. | |||
;<span id="ITIL Security Report">Information Security Report</span> | |||
:The Information Security Report provides other Service Management processes and IT Management with information related to Information Security issues. | :The Information Security Report provides other Service Management processes and IT Management with information related to Information Security issues. | ||
| Line 57: | Line 72: | ||
:A list of known security vulnerabilities compiled from input by third-party product suppliers. The list contains instructions for preventive measures and for the handling of security breaches once they occur. | :A list of known security vulnerabilities compiled from input by third-party product suppliers. The list contains instructions for preventive measures and for the handling of security breaches once they occur. | ||
;<span id="Security | ;<span id="ITIL Security Management Alert">Security Alert</span> | ||
:A warning produced by Information Security Management, typically released when outbreaks of security threats are foreseeable or already under way. The aim is to make sure that users and IT staff are able to identify any attacks and take appropriate precautions. | :A warning produced by Information Security Management, typically released when outbreaks of security threats are foreseeable or already under way. The aim is to make sure that users and IT staff are able to identify any attacks and take appropriate precautions. | ||
| Line 63: | Line 78: | ||
:A virtual repository of all Information Security Management data, usually stored in multiple physical locations. | :A virtual repository of all Information Security Management data, usually stored in multiple physical locations. | ||
;<span id="Test Report">Test | ;<span id="Test Report">Test Report</span> | ||
:A report of the preparation, progress and evaluation of a test, created for example during the various tests carried out by [[Availability Management|Availability]], [[IT Service Continuity Management|IT Service Continuity]] or [[IT Security Management|Information Security Management]]. | :A report of the preparation, progress and evaluation of a [[IT Security Management#ITIL Security Management Testing|test]], created for example during the various tests carried out by [[Availability Management|Availability]], [[IT Service Continuity Management|IT Service Continuity]] or [[IT Security Management|Information Security Management]]. | ||
;<span id="Underpinning-Information-Security-Policy">Underpinning Information Security Policy</span> | ;<span id="Underpinning-Information-Security-Policy">Underpinning Information Security Policy</span> | ||
:Underpinning Information Security Policies are specific policies complementing the [[IT Security Management#Security | :Underpinning Information Security Policies are specific policies complementing the [[IT Security Management#ITIL Security Policy|main Information Security Policy]] by setting binding rules for the use of systems and information as well as for the use and delivery of services, with the aim of improving information security. | ||
<p> </p> | <p> </p> | ||
== | == KPIs == | ||
* [[ITIL KPIs Service Design#ITIL KPIs Information Security Management|KPIs Information Security Management]] | |||
<p> </p> | |||
== | == Roles | Responsibilities == | ||
;Information Security Manager - Process Owner | ;<span id="Information Security Manager">Information Security Manager - Process Owner</span> | ||
:The Information Security Manager is responsible for ensuring the confidentiality, integrity and availability of an organization’s assets, information, data and IT services. | :The Information Security Manager is responsible for ensuring the confidentiality, integrity and availability of an organization’s assets, information, data and IT services. He is usually involved in an organizational approach to Security Management which has a wider scope than the IT service provider, and includes handling of paper, building access, phone calls etc., for the entire organization. | ||
<p> </p> | <p> </p> | ||
== | {| border="1" cellpadding="5" cellspacing="0" style="text-align:center;" valign="top" | ||
|- | |||
| valign="top" colspan="7" style="background:#ffffdd;" align="center"| '''Responsibility Matrix: ITIL Security Management''' | |||
|- | |||
! width="50%" align="center" style="background:#ffffee;" | ITIL Role | Sub-Process | |||
! style="background:#ffffee;" | [[IT Security Management#Information Security Manager|Information Security Manager]] | |||
! style="background:#ffffee;" | Service Owner[[#ITIL Security Roles|<small>[3]</small>]] | |||
! style="background:#ffffee;" | Applications Analyst[[#ITIL Security Roles|<small>[3]</small>]] | |||
! style="background:#ffffee;" | Technical Analyst[[#ITIL Security Roles|<small>[3]</small>]] | |||
! style="background:#ffffee;" | IT Operator[[#ITIL Security Roles|<small>[3]</small>]] | |||
! style="background:#ffffee;" | Facilities Manager[[#ITIL Security Roles|<small>[3]</small>]] | |||
|- | |||
| align="left" |[[#ITIL Security Management Controls|Design of Security Controls]] | |||
| A[[IT Security Management#Accountable|<small>[1]</small>]]R[[IT Security Management#Responsible|<small>[2]</small>]] | |||
| R | |||
| R | |||
| R | |||
| | |||
| | |||
|- | |||
| align="left" |[[#ITIL Security Management Testing|Security Testing]] | |||
| AR | |||
| | |||
| | |||
| | |||
| R | |||
| R | |||
|- | |||
| align="left" |[[#ITIL Security Management Incidents|Management of Security Incidents]] | |||
| AR | |||
| | |||
| | |||
| | |||
| | |||
| | |||
|- | |||
| align="left" |[[#ITIL Security Management Review|Security Review]] | |||
| AR | |||
| | |||
| | |||
| | |||
| | |||
| | |||
|- | |||
|} | |||
<p> </p> | |||
'''Remarks''' | |||
<span id="Accountable">[1] ''A: Accountable'' according to the RACI Model: Those who are ultimately accountable for the correct and thorough completion of the Information Security Management process.</span> | |||
<span id="Responsible">[2] ''R: Responsible'' according to the RACI Model: Those who do the work to achieve a task within ITIL Security Management.</span> | |||
<span id="ITIL Security Roles">[3] siehe [[Roles within ITIL V3|→ Role descriptions ...]]</span> | |||
<p> </p> | |||
<!-- This page is assigned to the following categories: --> | <!-- This page is assigned to the following categories: --> | ||
[[Category:ITIL V3]][[Category:ITIL process]][[Category:Service Design|Information Security Management]][[Category:Information Security Management|!]] | [[Category:ITIL V3]][[Category:ITIL 2011]][[Category:ITIL process]][[Category:Service Design|Information Security Management]][[Category:Information Security Management|!]] | ||
<!-- --- --> | <!-- --- --> | ||
Revision as of 17:58, 30 November 2011
<seo metakeywords="information security management, itil security management, security management itil, itil security management process, security management process" metadescription="Information Security Management: ITIL process definition - Sub-processes - Terms - Additional information on Information Security Management." />

Overview
Objective: Information Security Management aims to ensure the confidentiality, integrity and availability of an organization's information, data and IT services. ITIL Security Management usually forms part of an organizational approach to security management which has a wider scope than the IT Service Provider.
Part of: Service Design
Process Owner: Information Security Manager
Process Description
ITIL V3 treats Information Security Management as part of the Service Design core volume, resulting in a better integration of this process into the Service Lifecycle (the previous ITIL version provided guidance on Security Management in a separate book). The process was updated to account for new information security concerns.
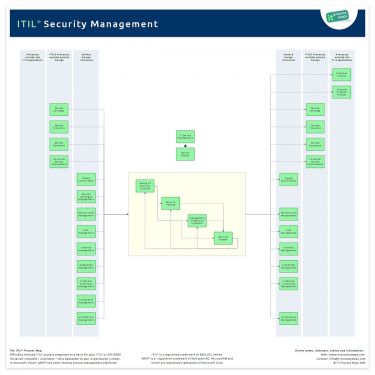
ITIL does not provide a detailed explanation of all aspects of Information Security Management, as there are dedicated and more detailed standards available (see, for example, ISO 27001). Rather, ITIL highlights the most important activities and assists in identifying interfaces with other Service Management processes.
Following the introduction of Design Coordination in ITIL 2011 the information flows have been adapted. The process overview of ITIL Security Management (.JPG) is showing the most important interfaces (see Figure 1).
Sub-Processes
These are the Information Management sub-processes and their process objectives:
- Design of Security Controls
- Process Objective: To design appropriate technical and organizational measures in order to ensure the confidentiality, integrity, security and availability of an organization's assets, information, data and services.
- <span="ITIL Security Management Testing">Security Testing
- Process Objective: To make sure that all security mechanisms are subject to regular testing.
- Management of Security Incidents
- Process Objective: To detect and fight attacks and intrusions, and to minimize the damage incurred by security breaches.
- Security Review
- Process Objective: To review if security measures and procedures are still in line with risk perceptions from the business side, and to verify if those measures and procedures are regularly maintained and tested.
Definitions
The following ITIL terms and acronyms (information objects) are used in ITIL Security Management to represent process outputs and inputs:
- Availability/ ITSCM/ Security Testing Schedule
- A schedule for the regular testing of all availability, continuity and security mechanisms, jointly maintained by Availability, IT Service Continuity and Information Security Management.
- Event Filtering and Correlation Rules
- Rules and criteria used to determine if an Event is significant and to decide upon an appropriate response. Event Filtering and Correlation Rules are typically used by Event Monitoring systems. Some of those rules are defined during the Service Design stage, for example to ensure that Events are triggered when the required service availability is endangered.
- Information Security Policy
- The main Information Security Policy contains an outline of the approach to ensure the security of IT services and systems. It is typically complemented by a set of more specific underpinning policies, e.g. policies on e-mail usage or remote system access. The Information Security Policy includes a list of security-related risks and existing or planned Security Controls to address those risks.
- Information Security Report
- The Information Security Report provides other Service Management processes and IT Management with information related to Information Security issues.
- Security Advisories
- A list of known security vulnerabilities compiled from input by third-party product suppliers. The list contains instructions for preventive measures and for the handling of security breaches once they occur.
- Security Alert
- A warning produced by Information Security Management, typically released when outbreaks of security threats are foreseeable or already under way. The aim is to make sure that users and IT staff are able to identify any attacks and take appropriate precautions.
- Security Management Information System (SMIS)
- A virtual repository of all Information Security Management data, usually stored in multiple physical locations.
- Test Report
- A report of the preparation, progress and evaluation of a test, created for example during the various tests carried out by Availability, IT Service Continuity or Information Security Management.
- Underpinning Information Security Policy
- Underpinning Information Security Policies are specific policies complementing the main Information Security Policy by setting binding rules for the use of systems and information as well as for the use and delivery of services, with the aim of improving information security.
KPIs
Roles | Responsibilities
- Information Security Manager - Process Owner
- The Information Security Manager is responsible for ensuring the confidentiality, integrity and availability of an organization’s assets, information, data and IT services. He is usually involved in an organizational approach to Security Management which has a wider scope than the IT service provider, and includes handling of paper, building access, phone calls etc., for the entire organization.
| Responsibility Matrix: ITIL Security Management | ||||||
| ITIL Role | Sub-Process | Information Security Manager | Service Owner[3] | Applications Analyst[3] | Technical Analyst[3] | IT Operator[3] | Facilities Manager[3] |
|---|---|---|---|---|---|---|
| Design of Security Controls | A[1]R[2] | R | R | R | ||
| Security Testing | AR | R | R | |||
| Management of Security Incidents | AR | |||||
| Security Review | AR | |||||
Remarks
[1] A: Accountable according to the RACI Model: Those who are ultimately accountable for the correct and thorough completion of the Information Security Management process.
[2] R: Responsible according to the RACI Model: Those who do the work to achieve a task within ITIL Security Management.
[3] siehe → Role descriptions ...